Secure access to approval tasks with OAuth Proxy
In previous article, Approval Tasks for Tekton has been introduced. Though that version lacked support for authentication to first of all secure the application and second to simplify usage for approvers - no need to manually enter user id or email to verify they are eligible to work on given approval task.
This article will exmplain on high level what to do to secure Automatiko Approval Tasks for Tekton by using OAuth Proxy as a side car container.
OAuth Proxy allows to use various providers, to name the few
- Google (default one)
- Azure
- GitHub
- GitLab
- and much more, see the complete list
First of all, in GitHub you need to create an application. Just go to https://github.com/settings/developers and create it
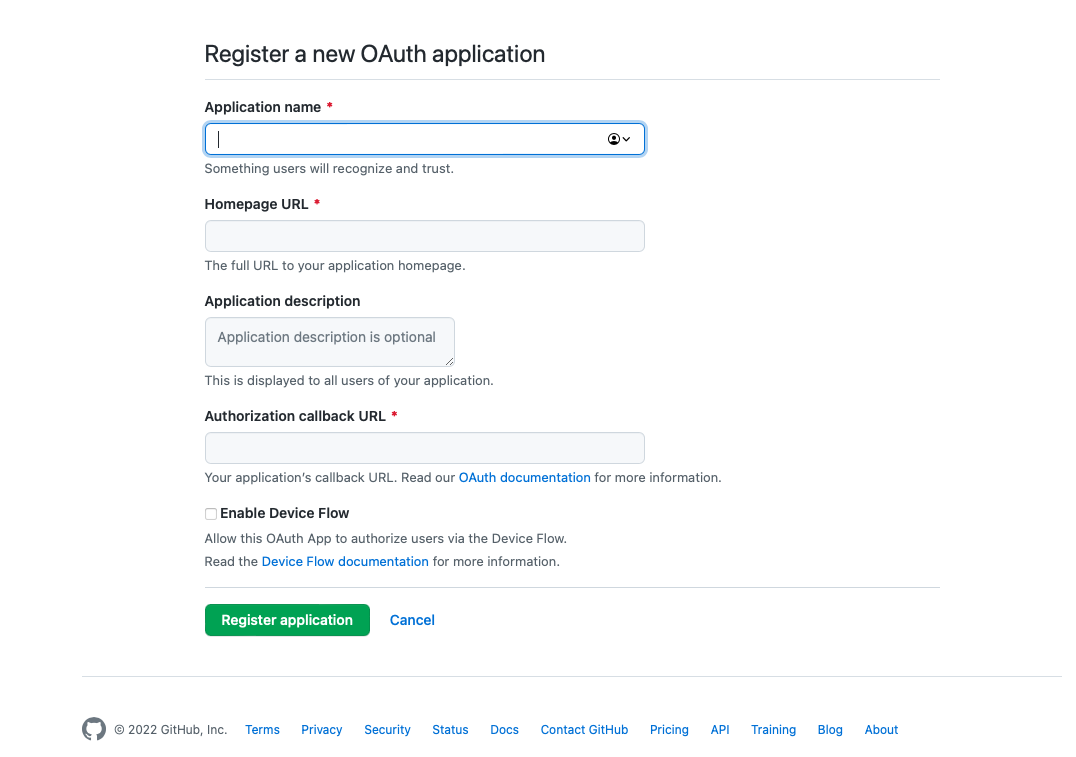 GitHub application creation.
GitHub application creation.
Make sure that the Authorization callback URL is set to your domain name and has following path /oauth2/callback.
So it could look like this https://approvals.mycompany.com/oauth2/callback
This will give you all the details you need to know to configure OAuth Proxy as side car container. Especially important ones are
- client id
- client secret
Let's configure the Approval Tasks deployment to make use of OAuth based authentication with GitHub as provider. This will consists of following additions to the default deployment manifest file.
- enable
securedprofile via environment variables - add second (
oauth-proxy) container - configure service to use OAuth Proxy instead the Approval Task
Enable secured profile via environment variables
Automatiko Approval Task come with various application profiles (like email, secured etc). Here we need to enable the secured profile
- name: QUARKUS_PROFILE
value: secured
Add second (oauth-proxy) container
Add new container into the deployment object that will run as side car to the Approval Tasks container
- name: oauth-proxy
args:
- --provider=github
- --https-address=
- --http-address=:8888
- --email-domain=*
- --prefer-email-to-user=true
- --upstream=http://localhost:8080
- --client-id=GITHUB_CLIENT_ID
- --client-secret=GITHUB_CLIENT_SECRET
- --cookie-secret=0rM16Iv8aSvlOZYXuabusXO98_y6Yf7QYjcIhXk67Dw=
- --pass-access-token=true
image: quay.io/oauth2-proxy/oauth2-proxy
imagePullPolicy: IfNotPresent
ports:
- name: oauth-proxy
containerPort: 8888
protocol: TCP
GITHUB_CLIENT_ID and GITHUB_CLIENT_SECRET with values for your GitHub application.
Note as well the cookie-secret that should be generated for production deployments explicitly, see various hase to generate it here
Configure service to use OAuth Proxy instead the Approval Task
As last step, let's change the service object to use OAuth proxy as entry point instead of the Approval Task
apiVersion: v1
kind: Service
metadata:
labels:
app.kubernetes.io/name: automatiko-approval-task
app.kubernetes.io/version: 0.1.0
name: automatiko-approval-task
spec:
ports:
- name: http
port: 80
targetPort: 8888
selector:
app.kubernetes.io/name: automatiko-approval-task
app.kubernetes.io/version: 0.1.0
type: ClusterIP
A complete manifest file with OAuth Proxy and GitHub can be found here
And that's it. Just deploy the Approval Task to your Kubernetes cluster and you can now enjoy secured Approval Tasks for Tekton pipelines.
This is just the minimal setup and further tuning can be done based on needs, like changing to another provider, using groups to authorize and so on.
As a final wrap, a short video demonstrating secured with OAuth Proxy and GitHub approval tasks can be watched below.
The source code of approval tasks can be found here
Thanks for reading and make sure to drop us feedback or ask questions about this article.
Photographs by Unsplash.